AWS GuardDuty
Prerequisites
To configure event collection, GuardDuty must first be enabled in your AWS account(s). Reference the following AWS documentation for information about enabling GuardDuty: Getting started with GuardDuty.
GuardDuty findings are automatically pushed to the event collector account using the AWS CloudWatch event bus. You do not need to complete any procedures in the following two AWS topics; they are presented here only to provide additional information about system communications.
- Sending and Receiving Events Between AWS Accounts
- Creating a CloudWatch Events Rule and Target for GuardDuty
Options for Monitoring Multiple AWS Accounts
If your organization utilizes multiple AWS accounts that will be monitored by GuardDuty, you have two configuration options:
- Single Master (Multiple Members): In this setup, one AWS account is configured as the GuardDuty master, and all other accounts (members) push their GuardDuty findings to the master. The master account then pushes the findings to the event collector. In this setup, only one master account per region needs to be configured to push findings to the event collector.
- Standalone: In this setup, GuardDuty is enabled in each AWS account that will be monitored. This setup requires that each account be individually configured to push findings to the event collector.
For help deciding on setup, consult this AWS topic: Managing multiple accounts in Amazon GuardDuty. The setup you choose will not affect analysis and reporting.
AWS Region Information
AWS GuardDuty is region-specific and must be enabled in every region individually. In the GuardDuty Management Console, in the upper-right corner of the screen, you can click the currently selected region to display a list of available regions. For each region in which you want to enable GuardDuty, you must select the region in this list, and then enable GuardDuty for that specific region.
Regardless of your organization's account setup, each region that either has a master or standalone GuardDuty configuration must be enabled to deliver findings to the event collector.
AWS Security Best Practice recommends that GuardDuty be enabled in all available AWS regions, even those you are not actively using. GuardDuty pricing is volume-based; therefore, fees are not incurred unless security findings are found in that particular region. ActiveEye supports the following AWS regions:
us-east-1, us-east-2, us-west-1, us-west-2, eu-central-1, eu-north-1, eu-west-1, eu-west-2, eu-west-3, ap-northeast-1, ap-northeast-2, ap-northeast-3, ap-south-1, ap-southeast-1, ap-southeast-2, ca-central-1, sa-east-1
Creating a Service Connector for Each AWS Account
For each AWS account that will be monitored via GuardDuty, a corresponding service connector must be created in ActiveEye. This separates the data into distinctly monitored entities with differing priorities and statuses.
In a single master setup, you only need to create service connectors for master AWS accounts. You do not need to create service connectors for the member AWS accounts.
- In ActiveEye, in the left pane, click Admin, and then click Service Connectors.
The Service Connectors page appears.
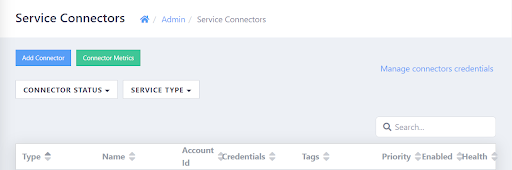
- In the upper-left corner of the page, click Add Connector.
A list of service connectors appears.
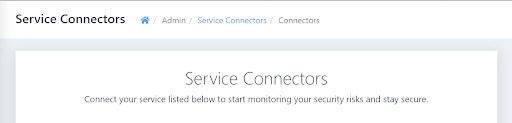
- Scroll down to the CLOUD INFRASTRUCTURE section, and then, in the AWS GuardDuty subsection, click the Add Connection button.
The Add Connector Account page appears. - In the Display Name box, enter a unique name.
- In the Account Number box, enter the 12-digit AWS account ID of the account to be monitored.
- Optionally, modify the priority level in the Priority box. Raising or lowering the priority will increase or decrease the visibility of alerts related to this service connector.
- If you do not want data ingestion to begin immediately once cloud accounts have been configured, clear the Enable Account check box. Otherwise, leave the check box selected.
- Click Add.
The AWS CloudTrail service connector is created. - Record the value in the Event bus ARN box. You will need it in the next procedure.
- As needed, repeat these steps until an AWS GuardDuty service connector has been created for each AWS account that will be monitored.
Configuring AWS Accounts to Push Findings to the Event Collector
The following procedure should be performed for every AWS account that has the GuardDuty service enabled in either the single master or standalone setup, and must be performed by an AWS IAM user with permissions to create CloudFormation stacks and modify CloudWatch Events rules.
In a single master setup, you only need to apply this configuration to master AWS accounts. You do not need to apply this configuration to the member AWS accounts.
- In the AWS console, in the upper-left corner of the screen, click Services.
- In the menu that appears, click Management & Governance, and then click CloudFormation.
The CloudFormation page appears. - Click the Create stack button, and then click With new resources.
The Create stack page appears.
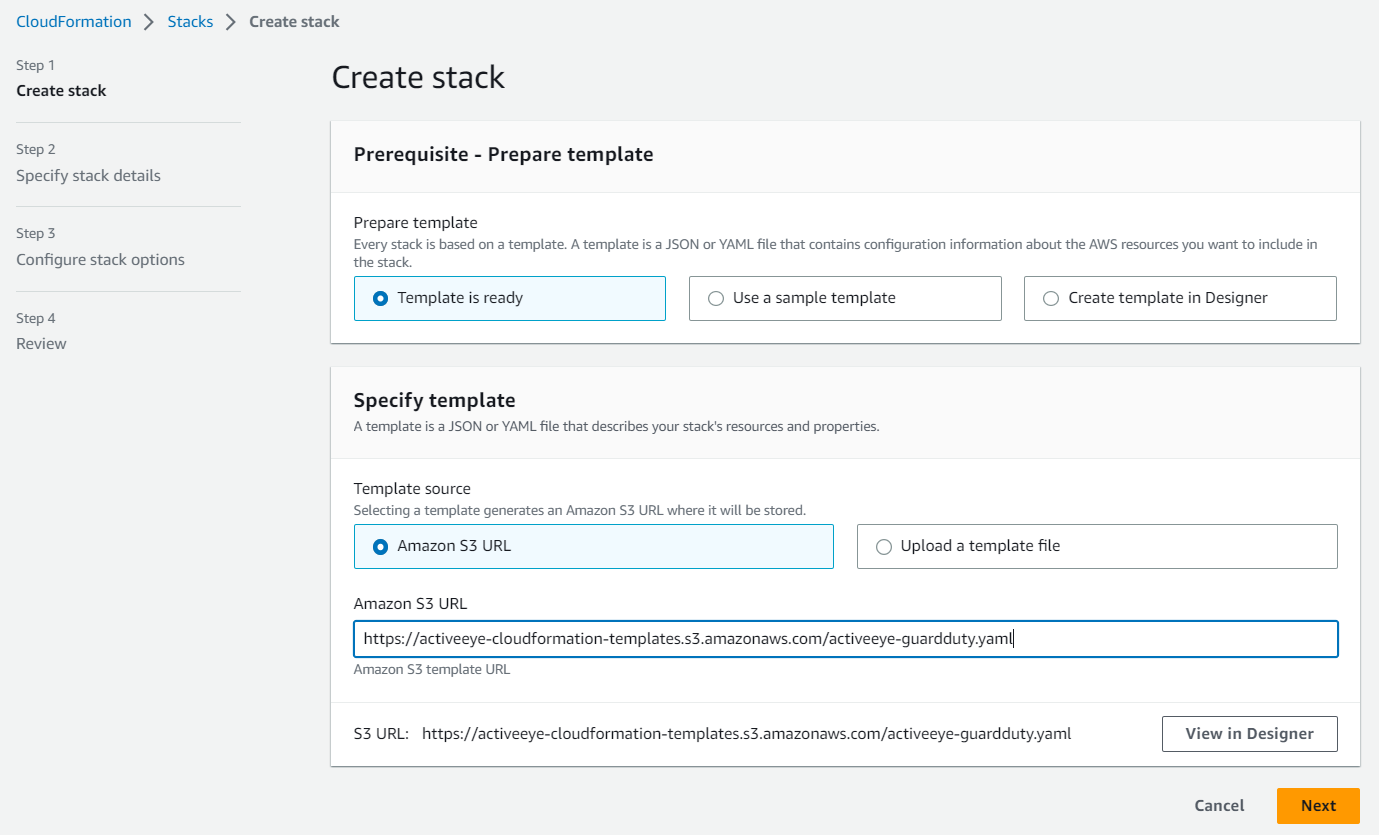
- With the Amazon S3 URL check box selected, depending on your environment, enter the appropriate text in the Amazon S3 URL box:
- For a commercial environment, enter the following: `https://activeeye-cloudformation-templates.s3.amazonaws.com/activeeye-guardduty.yaml`
- For a government environment, enter the following: `https://activeeye-cloudformation-templates.s3-us-gov-west-1.amazonaws.com/activeeye-guardduty.yaml`
- Click Next.
The Specify stack details page appears.
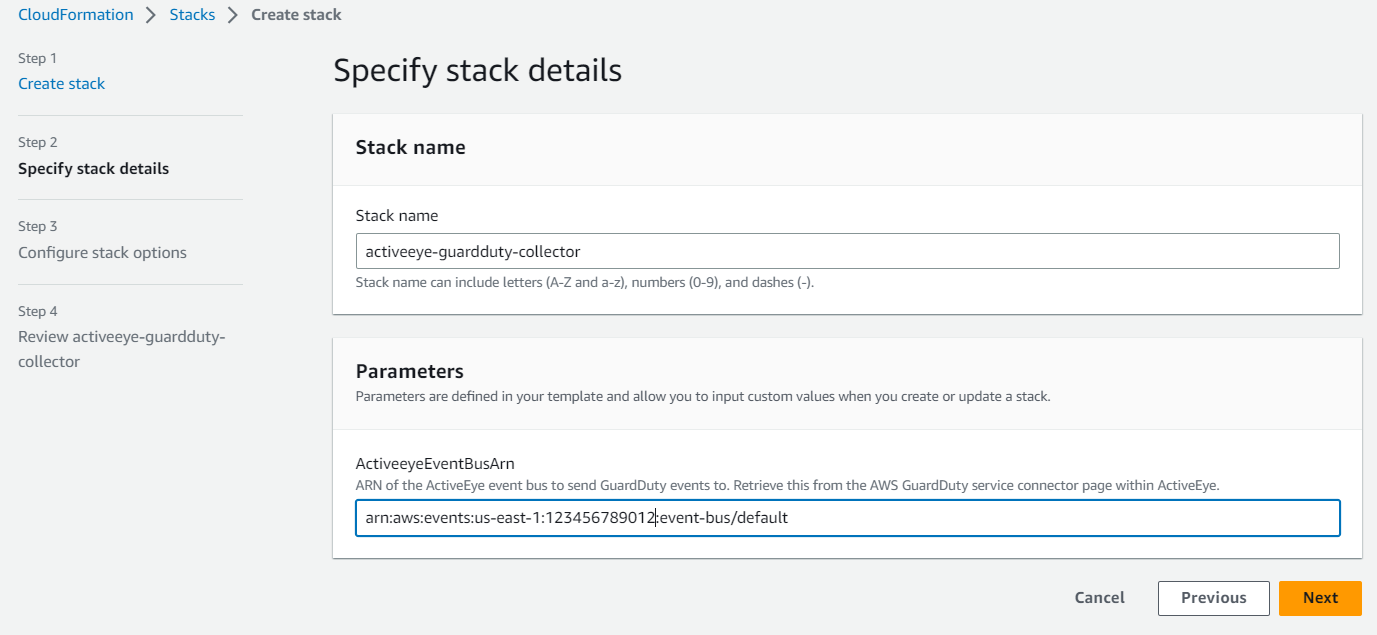
- In the Stack name box, enter the following: `activeeye-guardduty-collector`
- In the ActiveeyeEventBusArn box, enter the Event bus ARN value that you recorded in the previous procedure.
- Click Next.
The Configure stack options page appears. - Do not modify the default options. Click Next.
The Review page appears. - Select the I acknowledge that AWS CloudFormation might create IAM resources with custom names check box, and then click Submit.
- The stack is created, and a page displaying information about it appears.
- Repeat this procedure for each AWS account that needs to be monitored.