Microsoft Azure AD
Microsoft Licensing Notes
Activity reports are available for features that are licensed. If the license has a specific feature, access is available to the reports. For example, an Azure AD Premium P1 license is required to access self-service password audit reports.
Sign-in reports are available with the Azure AD Logins connector and require an Azure AD Premium license.
Many of the steps in this document are also required for set up of the Office365 and Azure Infrastructure service connectors. Follow the "Microsoft Office365 and Azure Infrastrucutre documentation for log collection" guide for setup of those connectors.
Client Information
Before logs can be pulled from your Microsoft Azure account, some information will need to be gathered. Some of these items may require additional setup within your Microsoft account and are documented in the subsequent sections.
In order to enable log retrieval, the following information will need to be collected:
- Directory ID - Sometimes referred to as the tenant or account id. This is a UUID string 36 characters in length
- Application ID - This is a UUID string 36 characters in length
- Secret Key - A random string approximately 44 characters in length
Additionally permissions will be required to be set to provide access to the log resources. These permissions are detailed below.
Configuring the Application Credentials
The first step will be to gather the information noted above and to setup an application registration for use.
Create an Application Registration
A new app registration must be created in the Azure Portal from which the Application ID and Secret Key will be copied.
- In the Microsoft Azure Portal select “Azure Active Directory”
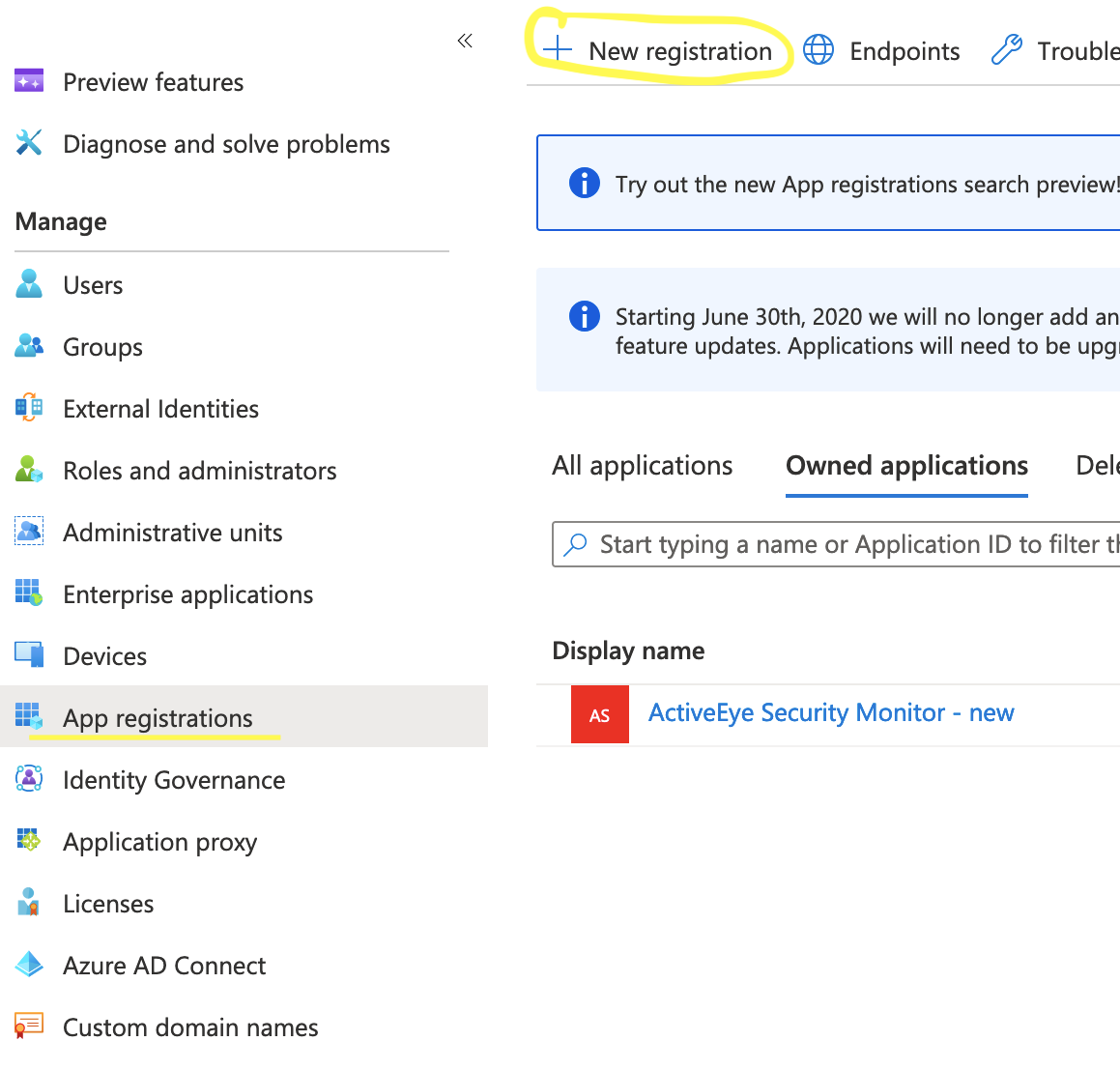
- Then select “App Registrations” under "Manage”
- Click the “New registration” button at the top
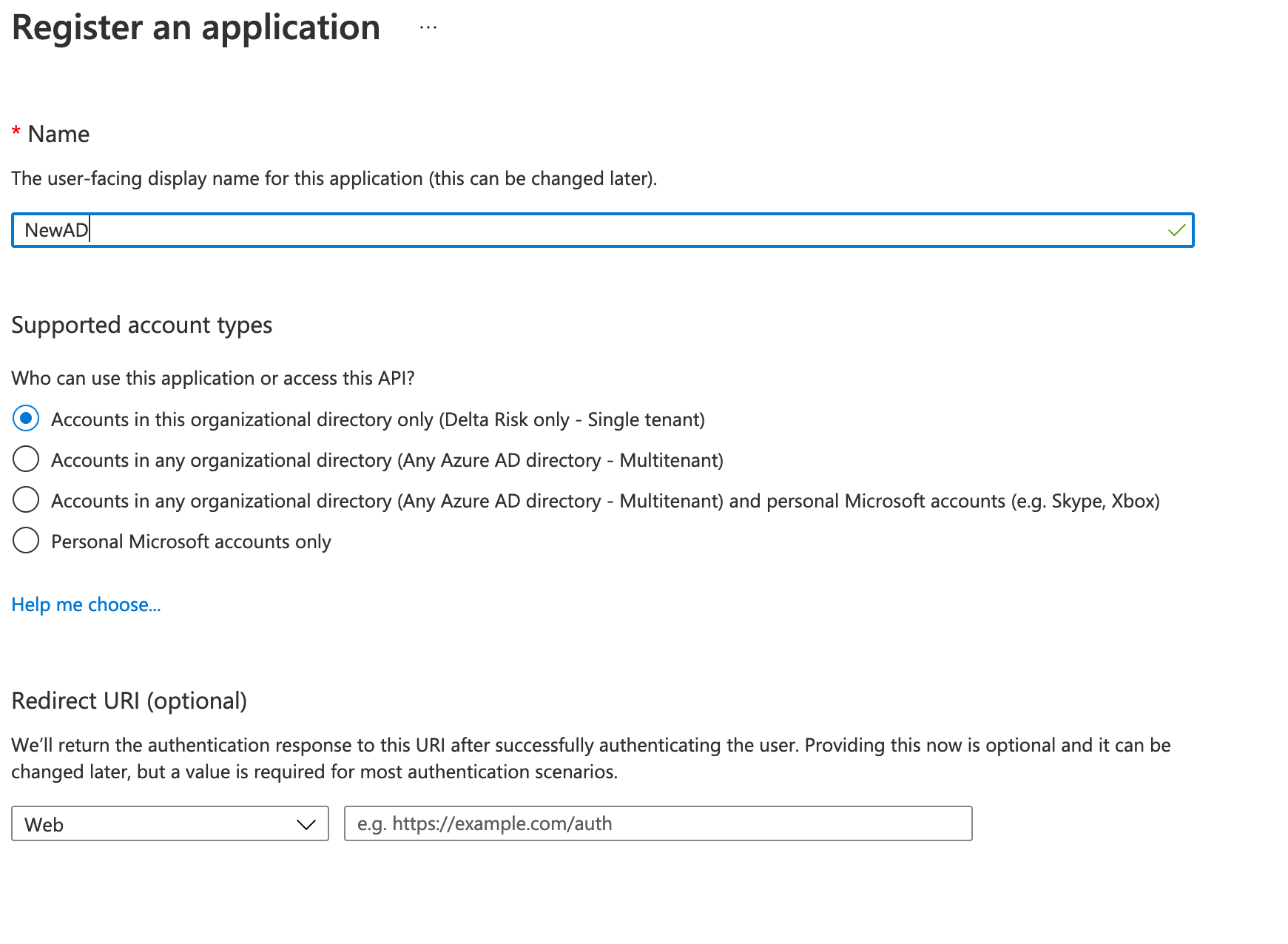
- Enter in the Name “ActiveEye Security Monitor”
- Under "Supported account types", select "Accounts in this organizational directory only (<Your Organization Here>)"
- Leave "Redirect URI (optional)" unmodified
- At the bottom, click "Register"
Get the Application and Directory ID
You will be redirected to the registered application page for your new application registration. From here:
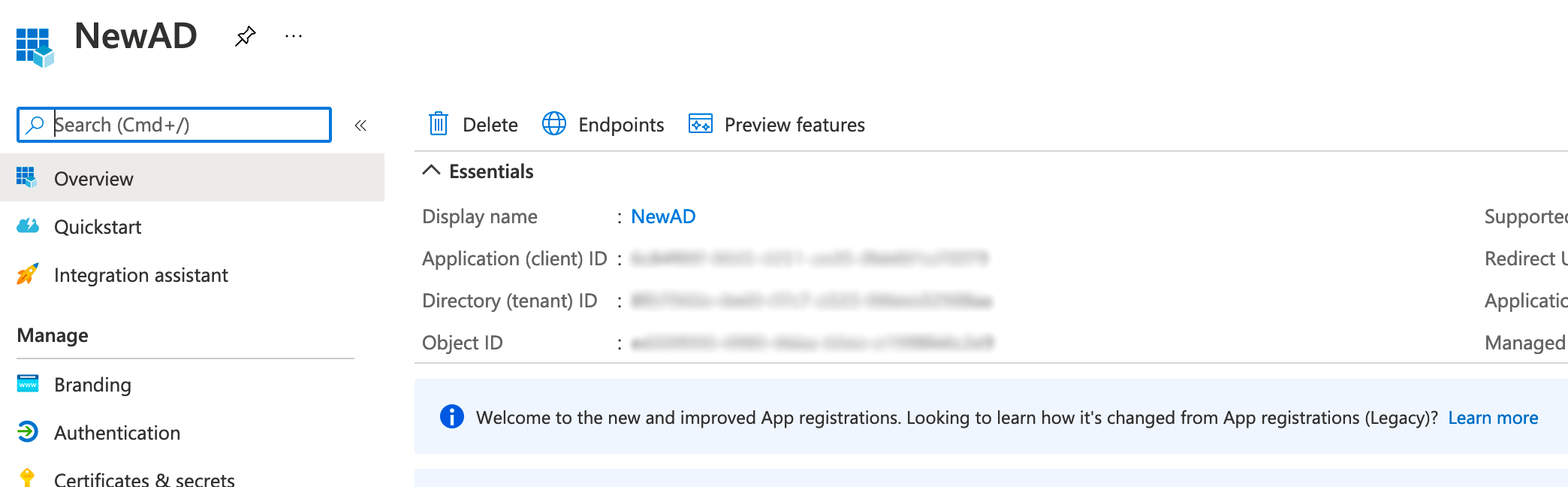
- Hover over "Application (client) ID" and the copy button will appear to the right. Click this button.
- Record this value as the "Application ID".
- Hover over "Directory (tenant) ID" and the copy button will appear to the right. Click this button.
- Record this value as the "Directory ID"
The value needed on this page is the Application ID, not the Object ID
Alternative to get the Directory ID (if absent in the above step)
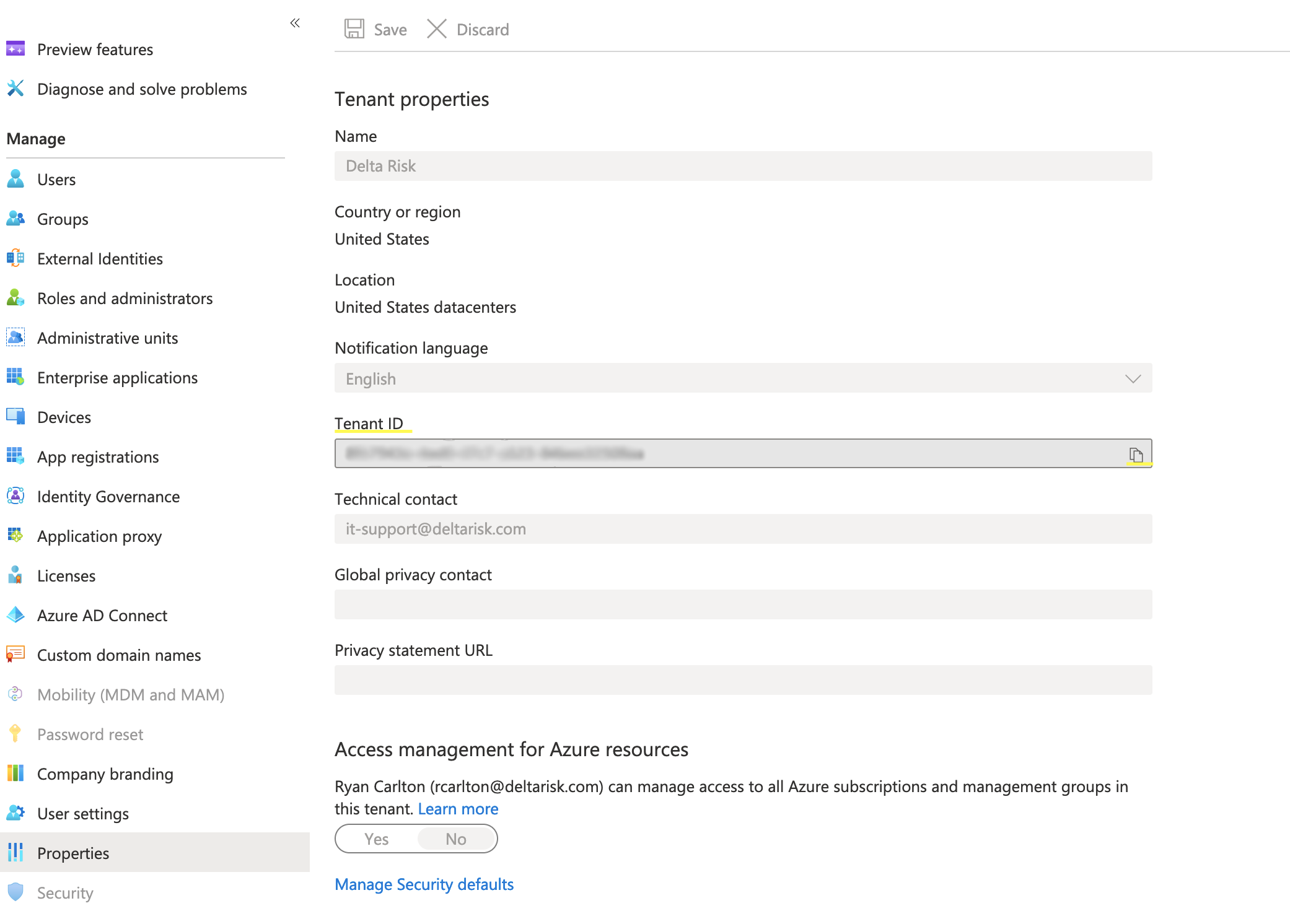
To get the Directory ID perform the following steps
- Login to the Microsoft Azure Portal with an administrator account.
- Select "Azure Active Directory" from "Favorites" on the left or "All services"
- Choose "Properties" under "Manage"
- Copy the "Tenant ID" using the copy button to the right of the Tenant ID
- Record this value and denote it as the "Directory ID"
Get the Secret Key
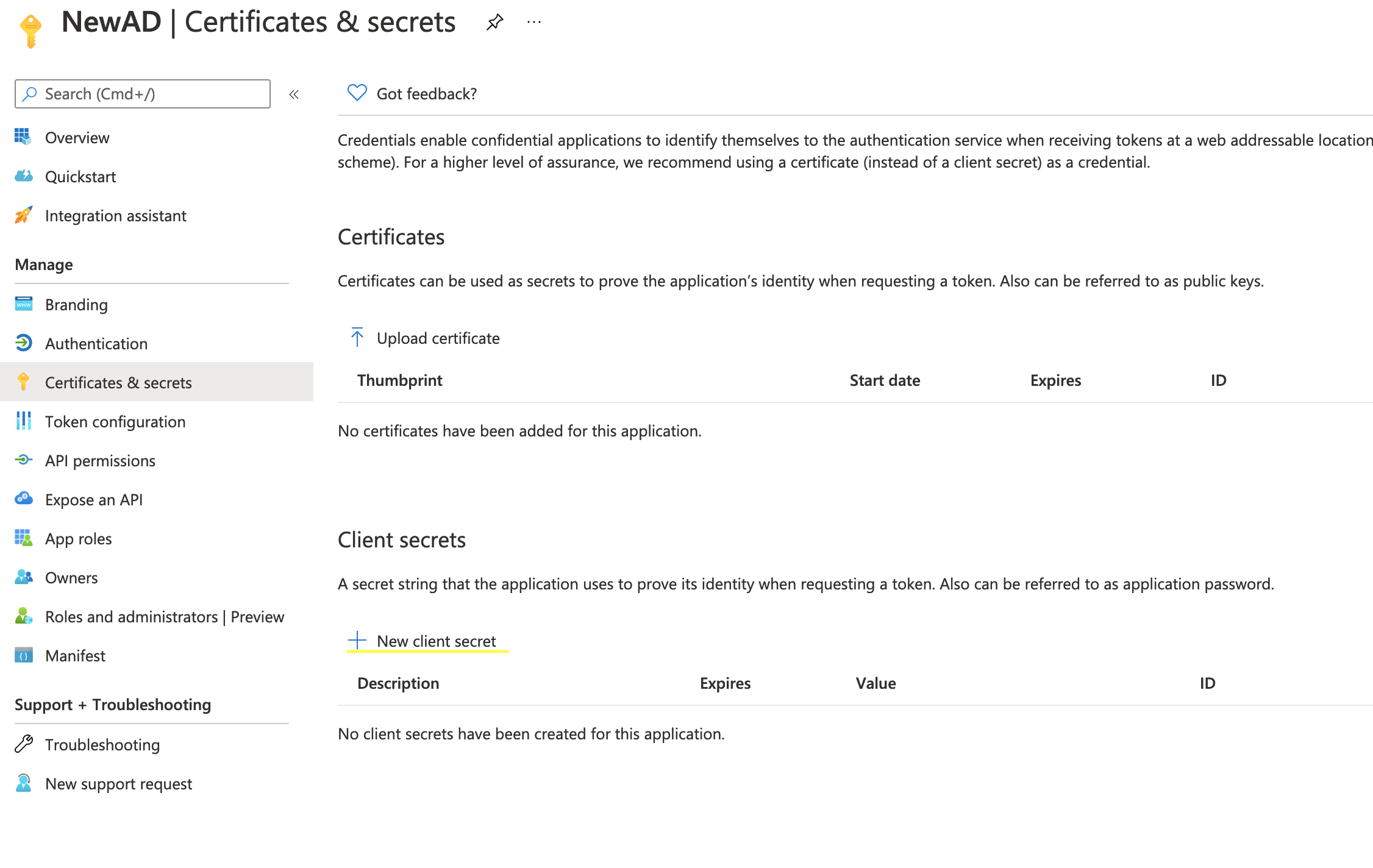
- From the registered application page where you obtained the Application ID, click "Certificates and secrets" from the left-side menu.
- Under "Client secrets", click "New client secret".
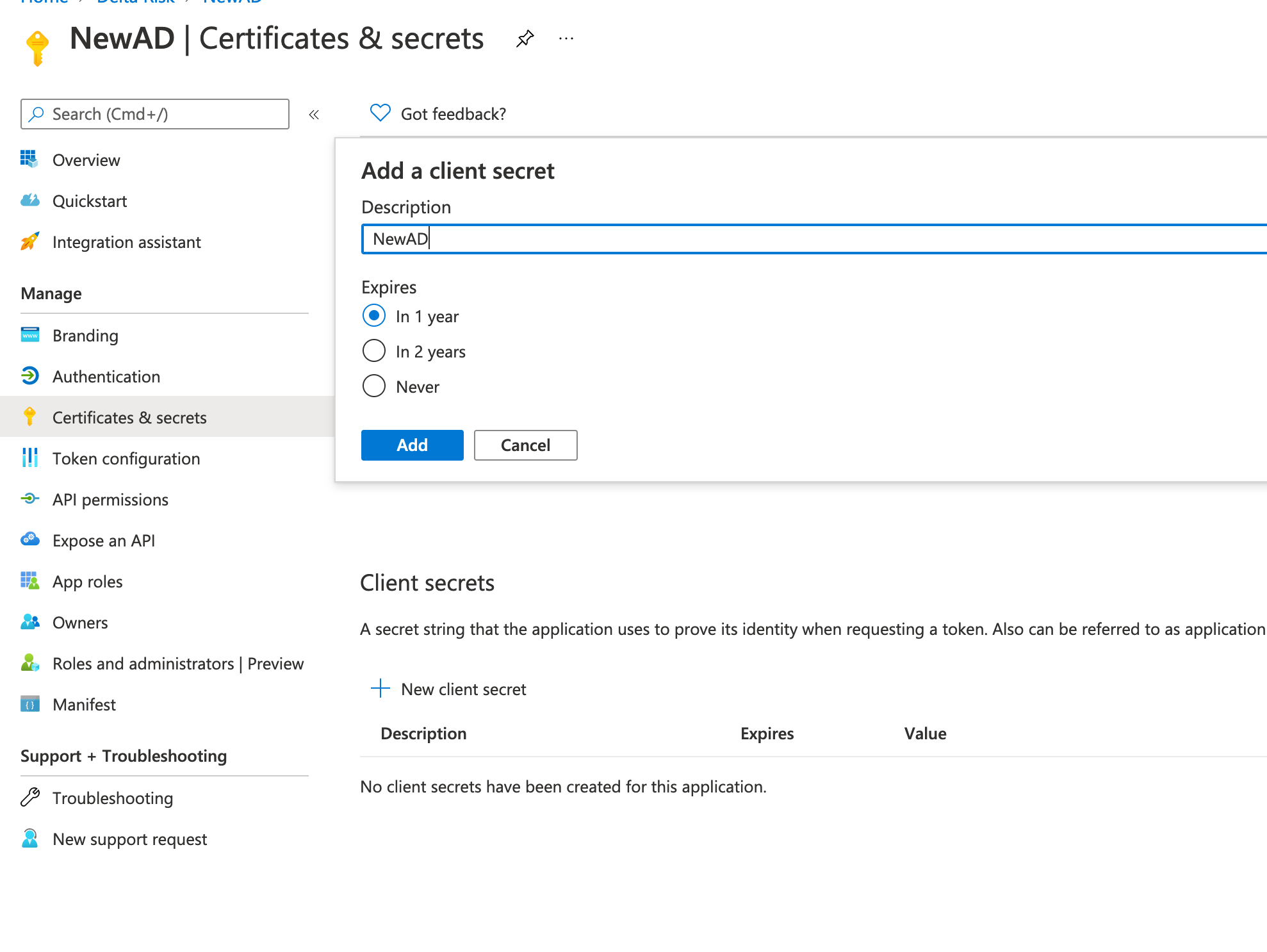
- For "Description", enter "ActiveEye Security Monitor".
- Select "Never", then click "Add".
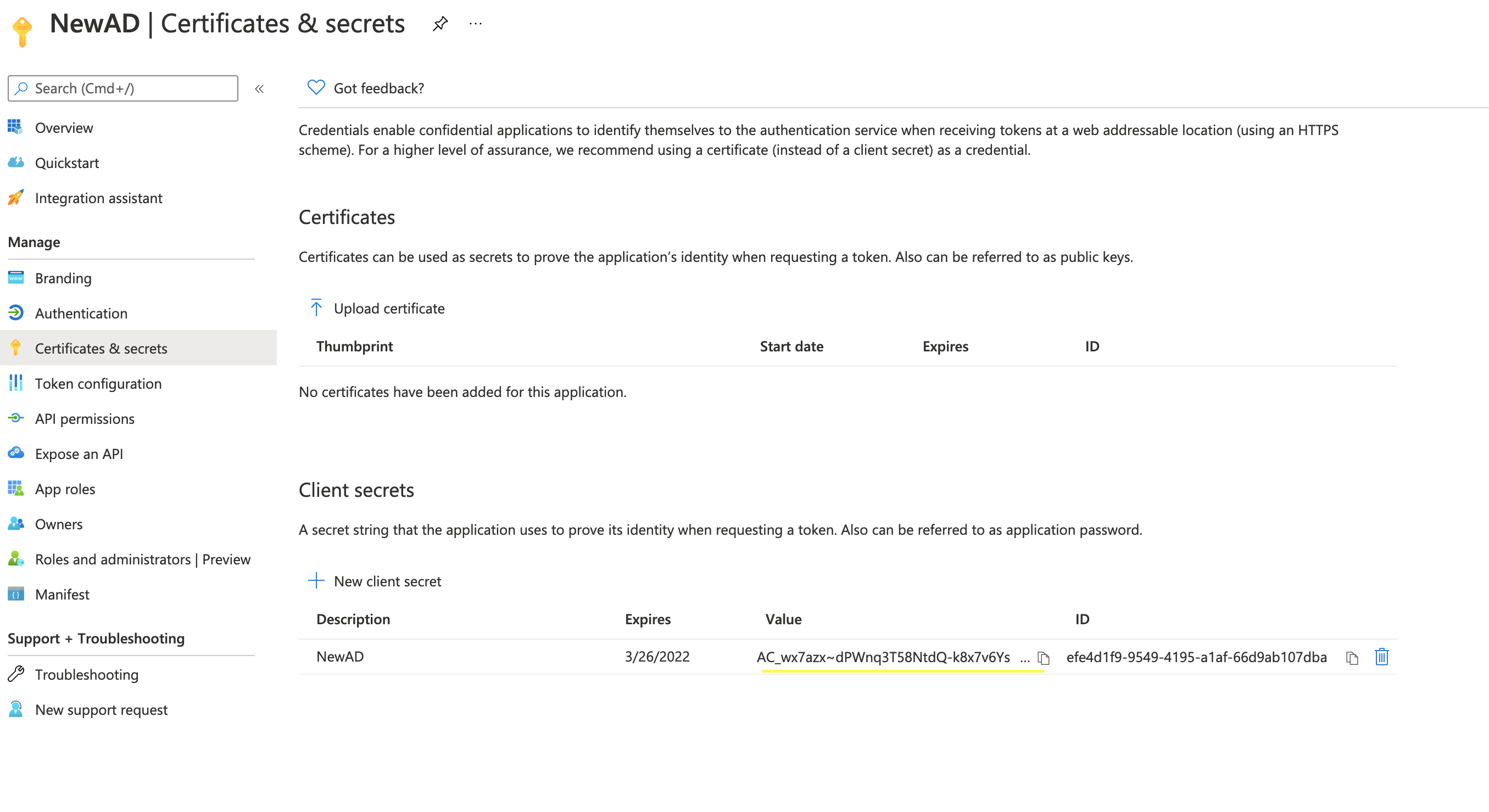
- When the screen refreshes, there will be a new entry under "Client secrets". Under "Value", there will be a copy button. Click this button.
- Record this value as the "Secret Key".
This is the only time this key will be available. If capturing this key was missed in the process then delete the original and create a new key.
Configure Microsoft Graph API Permissions (Required for Azure AD Logins Connector)
Now add permissions for Microsoft Graph.
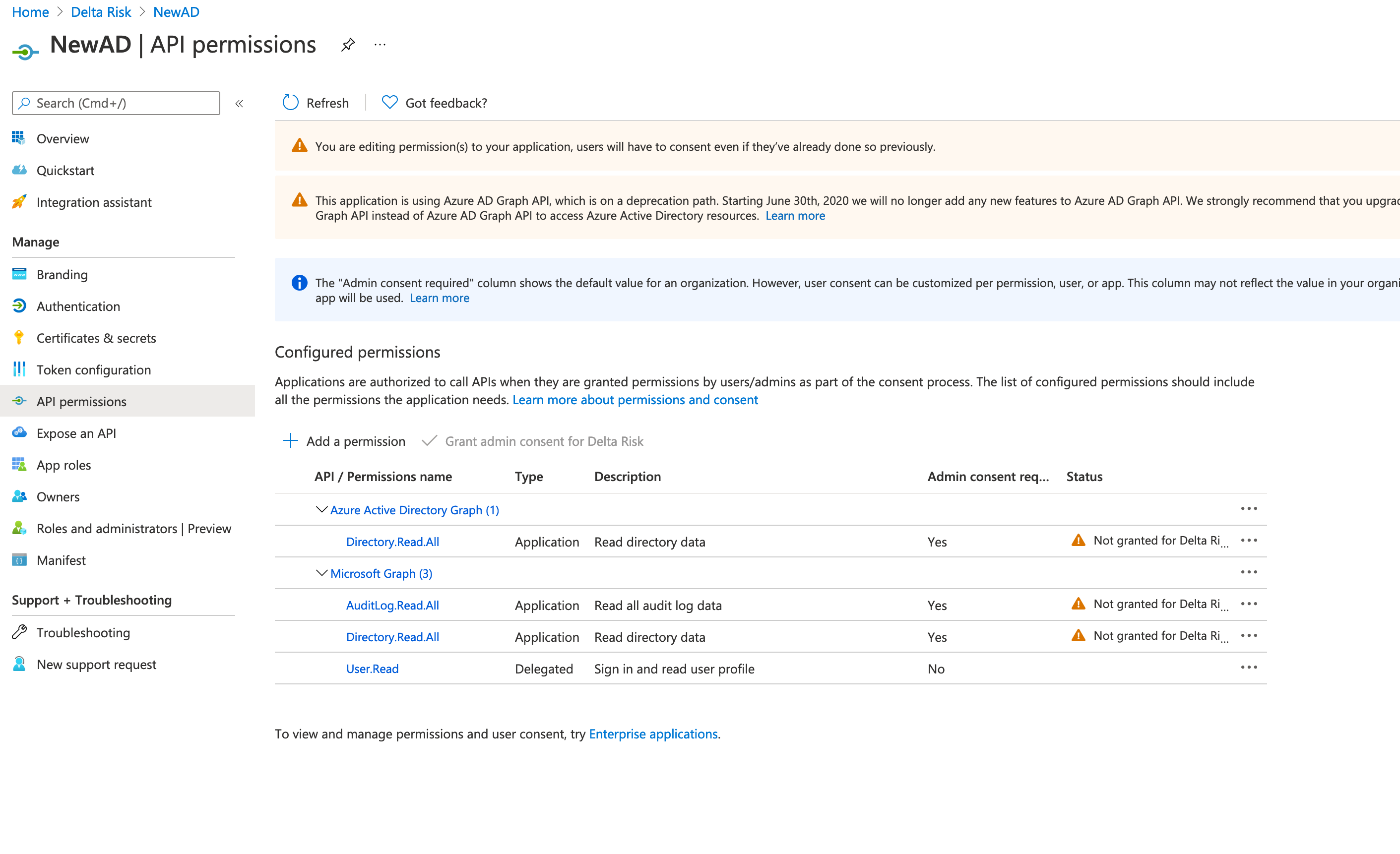
- From the left-side menu, click "API permissions".
- From the "API permissions" page, click "Add a permission", then find "Microsoft Graph" and click it.
- From the "Microsoft Graph" page, select "Application permissions". After redirecting to the new page, do the following:
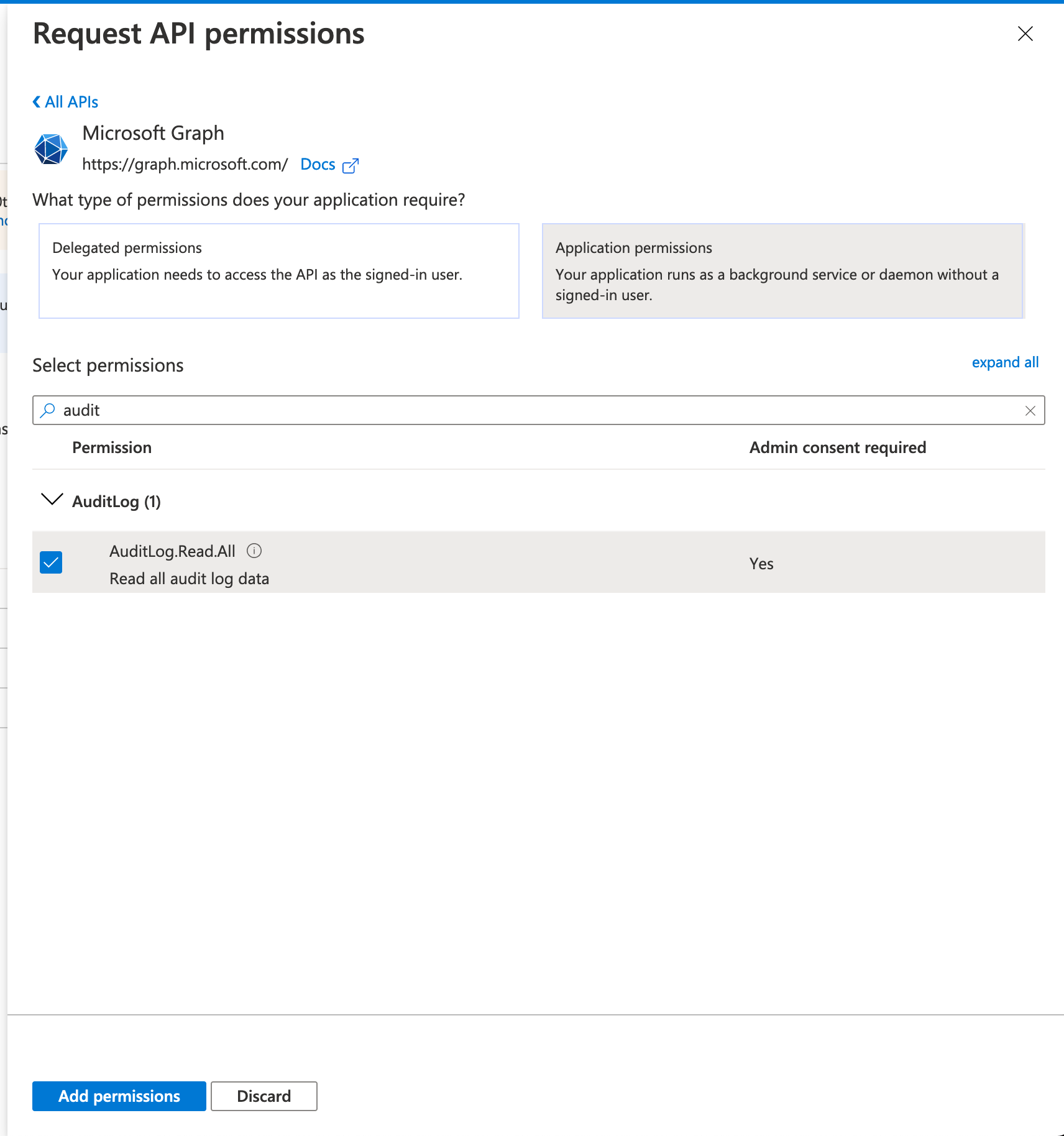
- Click "AuditLog" then check "Auditlog.Read.All"
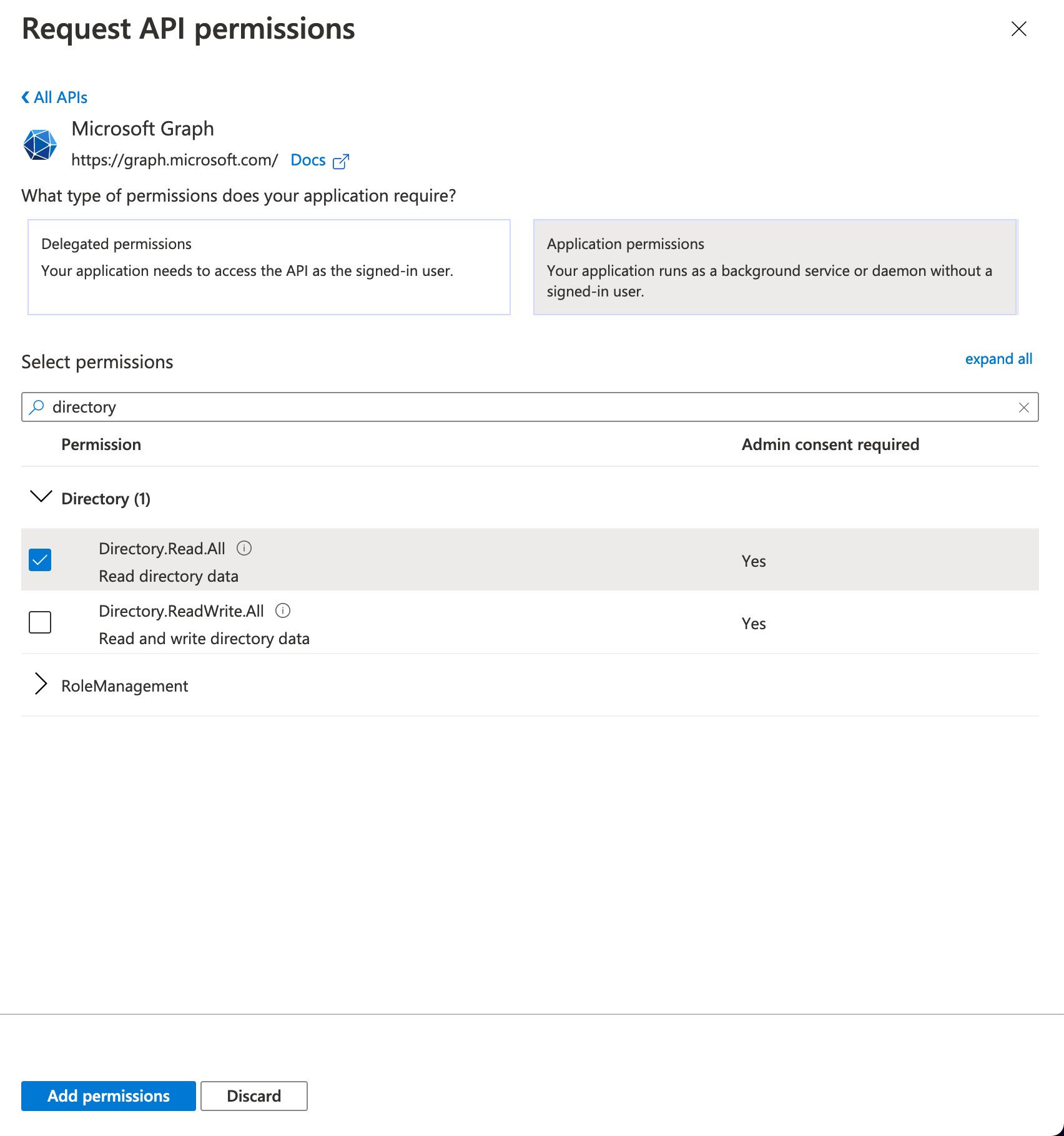
- Click "Directory" then check "Directory.Read.All" (Required for Azure AD Logins Connector)
- Click "Add permissions"
Grant Permissions
You must be a "Global Administrator" to perform this action. If you are not, you can ask an administrator do to so.
Anytime you make changes to app permissions an administrator must take the additional step to grant those permissions by performing the following steps. This step is critical and if not done event log collection will not function properly.
- On the next screen, click the "Grant Permissions" button
- Click "Yes" on the confirmation screen
- This will authorize the change to permissions that was made
STOP! MAKE SURE TO COMPLETE THIS STEP
Provide Client Information
The Directory ID, Application ID, Secret Key and possibly Subscription IDs and names should now be collected and available to complete the setup and start log collection. Provide these value to your service representative or use them for self service configuration following the "Configuring a new Service Connector for log collection" guide.