AWS VPC Flow Logs
Summary
AWS VPC Flow Logs allow for network traffic to be monitored and used for analysis. Presently Flow Logs can be enabled on VPCs, Subnets or individual Network Interfaces. Unfortunately there is no way to do so across all regions in an account do the following procedure must be applied on each VPC as applicable in a customer's AWS account.
See the following link for more information and background on VPC Flow Logs.
Create Cloudformation Stack Step by Step Instructions
The following steps will need to be performed by an AWS IAM User with permissions to create CloudFormation Stacks, IAM Roles. This is generally someone with AWS administrator rights. This step will need to be performed in each aws account where Flow Logs will be configured.
Login to the AWS console, click on Services, and under the Management Tools section click CloudFormation.
Click the “Create Stack” button
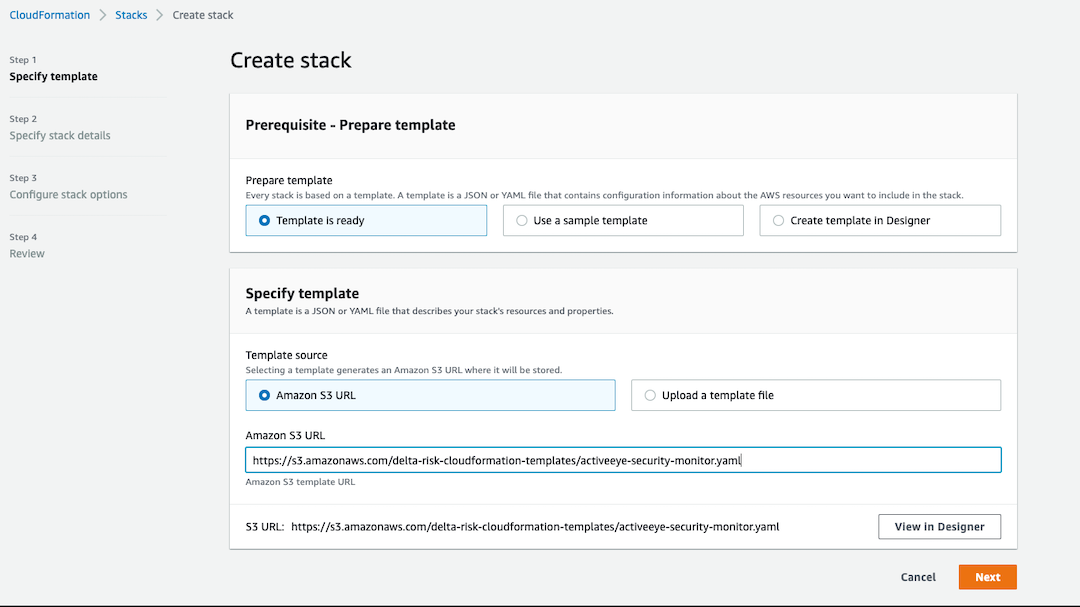
Click the “Specify an Amazon S3 template URL” radio button. Populate the text field with the following url then click “Next”.
For the stack URL use: https://s3.amazonaws.com/delta-risk-cloudformation-templates/activeeye-security-monitor.yaml
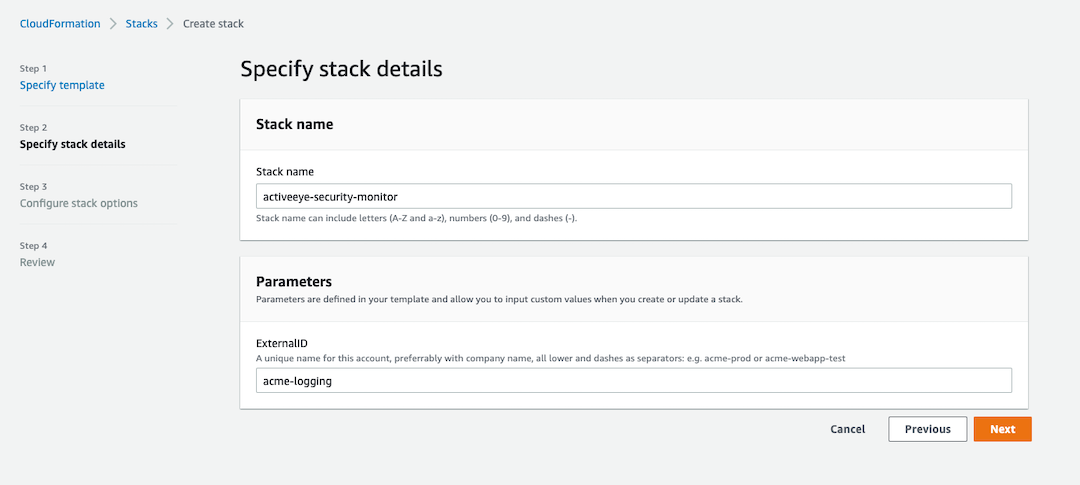
In the “Stack name” field, enter “activeeye-security-monitor”
In the “ExternalID” field, enter your customer name in a short form and possibly something descriptive of this account. Use a dash as a seperator if needed, no other special characters.
The External ID is not a secret in any way. It is simply an additional security measure that AWS recommends when allowing third parties to interact with your AWS resources. For more information on External IDs, see the following blog posting: How to Use External ID When Granting Access To your AWS Resources
Click “Next” and click through to the final confirmation screen. Check the acknowledgement and click “Create”.
When the stack is finished creating, select the stack and click the Outputs tab.
Copy the AccountID and ExternalID. This will be needed to create the ActiveEye Service Connector.
Repeat this step in each AWS account that contain Flow Logs that need to be monitored.
Creating Service Connectors per AWS Account
For each AWS account that will be monitored via Flow Logs a corresponding Service Connector will need to be created in ActiveEye. This is done to separate the data into distinctly monitored entities with differing priorities and status.
You must be an ActiveEye administrator to be able to perform the following steps.
Do these steps in ActiveEye:
- From the left hand menu, select ADMIN, SERVICE CONNECTORS.

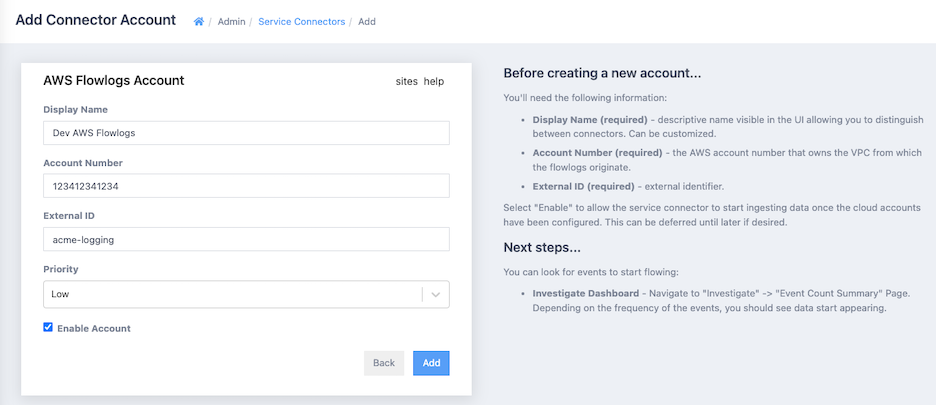
- Click the Add Connector button then Add Connection under AWS Flowlogs.
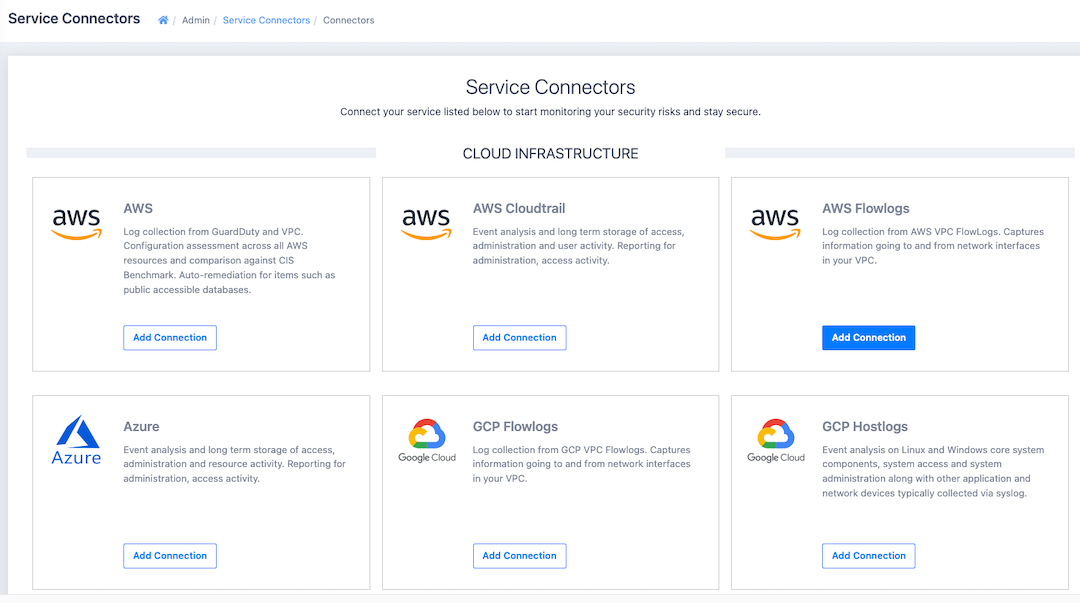
- Fill in the form
In the Display Name input, enter a distinguishable name for the AWS account. This name must be unique within ActiveEye for a particular connector type (in this case unique among AWS Flowlogs connector types). Enter the AWS account id immediately below. This will be a 12 digit number.
In the External ID input, paste the ExternalID set in the activeeye-security-monitor Cloudformation stack. The External ID in the service connector must exactly match the ExternalID parameter that was set in the Cloudformation stack.
Account priority may be adjusted to raise or lower the priority of the alerts created for this AWS account. Set the priority appropriately (e.g. dev test accounts could be low while accounts with sensitive information could be high). The priority can also be changed later, after the service connector has been created.
Click the Add button to finish setting up the Service Connector.
Repeat if necessary. Create individual service connectors for each AWS account to be monitored.
Configure Flow Logs
Flow Logs can be configured to be sent to either CloudWatch or to an S3 bucket. The S3 bucket method of delivery will be used in the following instructions.
- Login to the AWS console, click on Services, and under the Network section click VPC
- Select "Your VPCs" from the sidebar on the left
- Each VPC listed will have a "Flow Logs" tab when the VPC has been selected
- Click the "Create flow log" button
- Select the Filter "All"
- Choose "Send to an S3 bucket"
- Paste in the following into the S3 bucket ARN field:
arn:aws:s3:::delta-risk-flowlog-ingest
- Click the Create button.
For Further information on setting up Flow Logs to an S3 bucket see Publishing Flow Logs to Amazon S3
If there are more than one VPC to be monitored in additional regions, repeat the process above for each VPC to be monitored. Additionally repeat for any additional AWS accounts.
Provide Account Information
Provide the Account ID values to your service representative or use them for self service configuration following the <a class="internal" href="/setup/app_account#configuring-a-new-service-connector-for-log-collection" guide.